What is malvertising and how to stay safe online

Malvertising (short for malicious advertising) is when attackers use online ads to spread malware. Instead of hacking websites directly, they hide harmful code inside ads that are delivered through legitimate ad networks. Because these systems involve many intermediaries such as advertisers, exchanges, and publishers, harmful ads can sometimes make their way onto trusted sites.
Most online ads are safe, but the sheer scale of the advertising ecosystem means a small number of malicious ads can get through. If they do, they may redirect you to phishing pages, install malware, or exploit browser vulnerabilities if a weakness exists.
In this guide, you’ll learn how malvertising works, the most common attack types, and how to stay safe with smarter browsing habits and privacy tools.
How does malvertising work?
Many websites use third-party ad networks to display ads. Cybercriminals exploit this system by hiding malicious code inside ads. This allows infected ads to appear on legitimate sites, often without the site owner’s immediate awareness.
Once an infected ad is live, it can reach many websites through the ad network’s supply chain. When a browser loads one of these ads, the malicious script can:
- Redirect the browser to a phishing or exploit page.
- Trigger a “drive-by” download that installs malware, sometimes without any clicks if a vulnerability exists.
- Collect browser data and device information for later attacks.
- Try to exploit unpatched plugins or outdated software.
How ad networks are exploited
Ad networks automate the buying and placement of digital ads, letting publishers earn revenue and advertisers reach large audiences. That same automation gives attackers an opportunity to spread malware at scale.
Attackers exploit ad networks in several ways:
- Submitting poisoned ads: An attacker attempts to buy ad space and embed a redirect or malicious script within the ad content. While many networks screen for suspicious behavior, some harmful ads can still slip through and reach legitimate sites.
- Abusing third-party tags: Tracking pixels, analytics tags, and video ad scripts often load content from external servers. If those servers are compromised or malicious, they can deliver malware when the tag runs on a page.
- Exploiting supply-chain reselling and misconfigurations: Automated resale and complex routing can let low-quality or unvetted buyers place ads in ways publishers don’t fully control, increasing the chance malicious content gets through.
- Compromising an advertiser’s account: Attackers break into an advertiser’s account or ad-tech platform and inject malicious code into active campaigns. Because the ads still appear to come from a trusted provider, they can deliver harmful payloads without raising suspicion.
Types of malvertising attacks
There are several types of malvertising attacks, but most rely on social engineering. These ads use fear, urgency, or impersonation to trick you into clicking, and they appear more easily across many ad networks because they don’t rely on technical flaws.
There are also more advanced attacks that involve drive-by downloads, automatic redirects, or exploit kits. These depend on vulnerabilities in browsers or weaknesses in the broader ad-tech ecosystem. They’re far less common today because modern ad platforms restrict scripting and sandbox ad content.
Below are the most common types of malvertising attacks, ranging from deceptive pop-ups to silent code injections.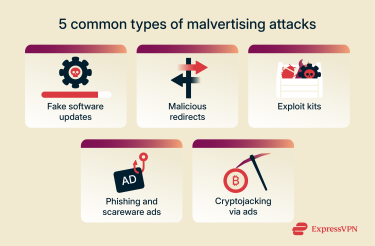
Fake software updates
Attackers sometimes use malicious ads to redirect you to malicious webpages that claim that your software is outdated or that your system is at risk, creating a sense of urgency. If you download and run the file they provide, it may install malware such as spyware or ransomware, although modern browsers and security tools will often block the attempt.
Malicious redirects
Some malvertising campaigns use rogue scripts that automatically redirect you to unsafe sites when an ad loads. These redirects can lead to fake tech-support pages, phishing sites, or exploit kits that try to install malware if a vulnerability exists. Hidden scripts may open the malicious site in a new tab or pop-up, where the scam or infection attempt takes place.
Exploit kits
An exploit kit is a collection of malicious tools hosted on a compromised server. When a user encounters a compromised ad, the kit scans their system for weaknesses such as outdated browsers or missing security patches. If it detects a flaw, it launches an attack designed for that specific vulnerability.
Phishing and scareware ads
As mentioned, some malicious ads don’t install malware directly but use fear or deception to manipulate users. These “scareware” banners might claim a virus has been detected or your personal data is exposed, followed by a fake security scan or paid cleanup offer. These services are fraudulent and can lead to further infection. Phishing ads also imitate trusted brands to harvest login credentials and credit card data.
Cryptojacking via ads
In some cases, attackers insert hidden cryptocurrency miners into ad scripts. When a compromised ad loads, it activates code that uses the victim’s CPU or GPU to mine cryptocurrency for the attacker. While less common than other forms of malvertising, cryptojacking through ads has been observed in several campaigns.
Identifying and detecting malvertising
Malvertising is difficult to spot because it can appear on legitimate websites through trusted ad networks. Infected ads are designed to look normal, so users rarely notice anything suspicious until after an attack occurs. Even so, there are a few warning signs that can help you recognize potential threats and reduce the risk of exposure before any real damage happens.
How to spot a malicious ad
Not every malicious ad looks suspicious, but many malvertising campaigns share common warning signs. Watch for ads that:
- Use urgent or alarming language, such as “Your device is infected!” or “Critical system update required.”
- Contain obvious spelling, grammar, or design errors.
- Redirect or open new pages unexpectedly, even without any clicks or interaction.
- Prompt direct downloads or display fake system alerts.
- Imitate trusted brands but link to unrelated or misspelled domains.
- Autoplay audio or video unexpectedly when the page loads.
Signs your device might be compromised
Once a malvertising attack succeeds, it often leaves traces. Watch for malware symptoms such as:
- Frequent redirects or pop-ups on legitimate websites.
- Noticeable system slowdowns, overheating, or a constantly running fan, which may suggest cryptojacking.
- New toolbars, browser extensions, or apps appearing without your consent.
- Repeated antivirus or firewall alerts, including fake ones.
- Unusual spikes in data or background network activity.
- Sudden changes to your browser’s homepage, search engine, or privacy settings.
Platforms commonly targeted
Malvertising isn’t limited to desktop web browsers. Attackers target any platform that serves digital ads, including:
- Windows, macOS, and Linux browsers, where outdated plugins or scripts can be exploited.
- Mobile devices, where in-app ads or free games can carry malicious code.
- Smart TVs and streaming boxes, which may run lightweight browsers that are more likely to lack strong security protections.
Malvertising vs. other threats
Malvertising often overlaps with other online threats, but it has a few differences.
Difference between malvertising and malware
Malware refers to any malicious software that infects a device, whether it’s installed without consent or downloaded by mistake. It can include trojans, spyware, ransomware, and computer worms.
Malvertising refers to the delivery method, not the malware itself. In malvertising, malicious ads act as the gateway for malware.
Malvertising vs. adware
While malvertising occurs on the web, adware resides on the device. The key difference lies in where and how each threat operates. As discussed, malvertising abuses third-party ad networks to spread infections through ads on websites. Adware, by contrast, is software installed on a device that continuously displays ads, often across different apps or browser windows.
How to protect yourself from malvertising
There’s no way to block every malicious ad, but good digital hygiene and layered security tools can significantly reduce exposure. Since malvertising exploits legitimate ad networks, prevention is about minimizing attack surfaces and making your system harder to compromise.
Effective prevention methods
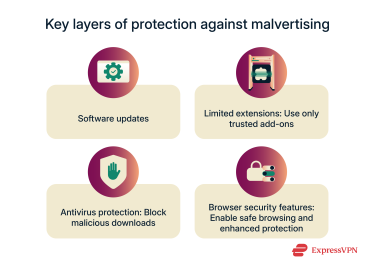 Reducing the risk of malvertising starts with simple, consistent habits. Here are some easy ways to strengthen your protection:
Reducing the risk of malvertising starts with simple, consistent habits. Here are some easy ways to strengthen your protection:
- Keep software up to date: Regularly install browser, plugin, and operating system updates through trusted domains to patch known software vulnerabilities.
- Limit browser extensions: Some outdated or untrustworthy extensions run scripts that malicious ad campaigns can exploit. It’s best to use only trusted, essential add-ons.
- Use a reputable antivirus app: Real-time scanning can detect drive-by downloads and block malicious payloads before they run.
- Enable browser security features: Modern browsers like Chrome, Edge, and Firefox include “Safe Browsing” or “Enhanced Protection” modes that block known malicious ad domains.
- Use a VPN: Some VPNs include tools that can block malicious sites or intrusive ads, adding another layer of protection against online threats.
Ad blockers and malvertising prevention
Ad blockers are one of the strongest defenses against malvertising because they stop most ads from loading in the first place. However, they’re not perfect. Harmful ads can still appear if they come from trusted domains, are loaded through external scripts, or bypass standard filtering methods.
So, to get the most out of an ad blocker, you should:
- Keep filters updated: Malvertising tactics change constantly, so make sure your ad blocker updates its filter lists automatically.
- Turn on extra protection: Many ad blockers include optional security or anti-tracking filters that can stop malicious ads and hidden scripts.
- Be cautious on unfamiliar sites: If a website asks you to disable your ad blocker, only do so if you fully trust it.
- Use a script manager for added control: Pairing your ad blocker with a tool that manages scripts can add another layer of defense against hidden malware.
How VPNs help reduce malvertising exposure
A virtual private network (VPN) can’t block malvertising, but it strengthens overall security. By encrypting traffic and masking your IP address, a VPN reduces how much ad scripts can track or profile you, especially on unsecured networks.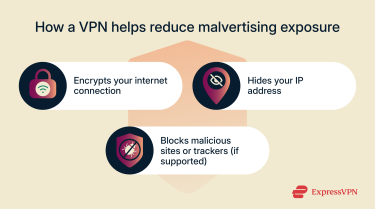
A good VPN can reduce exposure by:
- Encrypting connections on public Wi-Fi, where traffic manipulation such as injected ads or redirect scripts can occur on poorly configured networks.
- Using private, secure DNS resolvers to prevent DNS leaks and manipulation. Some VPNs also offer DNS-based threat filtering to block access to known malicious or tracker domains. For example, ExpressVPN provides this through its Threat Manager feature.
- Making it more difficult for ISPs and intermediaries to modify traffic, including injecting ads or trackers.
Some VPN providers, including ExpressVPN, also come with an ad blocker included. This tool filters most display ads and stops them from loading in your browser. It works across all major platforms, including Windows, macOS, Linux, Android, and iOS.
Choosing a trusted security suite
Modern security suites include web protection that can analyze ads and block some suspicious web scripts before they load.
When evaluating security software, look for tools that provide:
- Real-time web filtering and exploit protection: This helps to block malicious ad domains, redirects, and drive-by downloads before a page fully loads.
- Behavioral analysis and heuristic scanning: Instead of relying on known signatures, these systems detect suspicious ad behavior, like scripts trying to open hidden windows or download files silently.
- Browser integration: Some suites include plug-ins that scan ad content in real time, flag suspicious banners, or warn when a page connects to a known ad injection server.
- Cloud-based threat intelligence: Security tools that share real-time threat data across a global network can identify and block new malvertising campaigns quickly.
- Network-level protection: Premium suites often include advanced firewalls or DNS-filtering modules that can prevent requests to malicious advertising domains.
Safe browsing habits and best practices
Safe browsing habits can also lower the risk of exposure to malvertising. Here are some practical tips that can make a difference:
- Avoid clicking on pop-ups or flashy banners, even if they appear on reputable sites.
- Watch for odd redirects or fake login pages; close tabs that behave unexpectedly.
- Clear your browser cache and cookies regularly to remove stored scripts.
- Periodically review which sites have permission to show notifications or ads.
- Consider using a web browser with built-in anti-tracking features.
What to do if you encounter malvertising
Even if you’re careful, you may encounter malvertising. If you suspect exposure, it’s important to act quickly to contain the risk and remove potential malware.
First steps after clicking a malicious ad
If you suspect that an ad triggered a redirect or unwanted download:
- Run a full system scan: Use a reputable antivirus or security suite with updated definitions to check for potential infections. While no scan can catch every threat, it can often detect and remove most known malware or suspicious files.
- Clear web browser data: Delete cache, cookies, and temporary files that might store malicious scripts. Most mobile browsers include this option in their privacy or settings menu.
- Change your passwords: If the ad led to a fake login page and requested credentials, immediately reset any passwords you shared. You can use a tool like ExpressVPN Keys to generate and store secure passwords. Also, enable two-factor authentication, which provides an additional layer of safety when logging in.
- Restart only after scanning: Some malware reactivates on reboot. Ensure your system is fully clean before restarting, and consider scanning your device again to confirm.
- Update your browser and operating system: Installing the latest patches prevents reinfection via the same vulnerability.
Reporting malvertising (Google, social platforms, ad networks)
Reporting malvertising helps take down active campaigns and protects other users. Always collect details like the site visited, ad appearance, and URL before submitting a report. You can report malicious ads to:
- Google Ads: You can use Google’s Ad Center to report malicious ads. If ads come from Google’s ad network, you can right-click an ad and choose Why this ad? > Report ad to flag malicious or misleading content.
- Social media platforms: On Facebook and Instagram, click the three-dots menu on any ad and select Report Ad > Misleading or Scam. On X (Twitter), open the ad’s dropdown menu and select Report Ad > Suspicious or Spam.
- Ad networks: If the malicious ad appeared on a known published site (like a news outlet), contact their web admin and flag the infected ad slot. Major ad networks, like Google AdSense, have dedicated abuse-report forms where you can submit URLs and screenshots.
- Browser developers: Chrome, Firefox, and Edge all include built-in tools to report deceptive websites. When you open the page you believe is malicious, use the three-dot or three-line menu and go to Help > Report an Issue. This feature could also be labeled as “Report Deceptive Website” or “Report Unsafe Site.”
FAQ: Common questions about malvertising
What is an example of malvertising?
A common example of malvertising is a fake software update ad that you’ve been redirected to from a legitimate news or streaming website. The ad might claim your browser or media player is outdated and prompt you to “install the latest version.” Clicking the link can trigger a download or redirect you to a site hosting malware.
Can malvertising infect my device without clicking?
In rare cases, yes. Some malvertising campaigns can use hidden scripts or exploit kits that can run automatically when an ad loads in your browser, a technique known as a drive-by download. This type of attack tries to install malware in the background by exploiting unpatched software or browser vulnerabilities.
Modern browsers block most of these attempts, but keeping your system, browser, and security tools up to date is essential to stay protected.
Is malvertising found on reputable websites?
Unfortunately, yes. Attackers can distribute infected ads through legitimate ad networks that supply large, trusted websites. Even well-known news outlets or streaming platforms can unknowingly serve malvertising in the worst-case scenarios.
How do I remove malvertising from my browser or device?
To remove malvertising properly, run a full scan using a reputable antivirus or security suite, then reset your browser settings to default. Remove suspicious extensions or newly installed applications that coincide with the infection. For extra assurance, use an additional anti-malware scanner to catch any remaining files.
Do ad blockers fully stop malvertising?
Ad blockers significantly reduce the risk of malvertising but can’t guarantee complete protection. Some infected ads slip through if the server is from a trusted domain. Combining ad blocking with safe browsing practices, up-to-date software, and a VPN provides stronger overall protection.
Does using a VPN protect me from malicious ads?
Not all VPNs can block malicious ads, but they can help protect your traffic by encrypting connections and hiding your IP address. This limits tracking, profiling, and ad injection attempts from third parties. Some VPNs, like ExpressVPN, include an optional ad blocker and DNS filtering to filter display ads and block access to known malicious domains.
What to do if I clicked on a suspicious ad?
The first step after clicking a suspicious ad is to run a full antivirus scan, then clear your browser cache and cookies. If you entered login details on a suspicious page, change those passwords immediately and enable two-factor authentication for affected accounts.
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN