What is DNS TTL? Best practices for privacy and performance
Every time you visit a website, your device sends a request to a Domain Name System (DNS) server, which looks up the domain name and then sends you the numerical IP address associated with it. The results are stored temporarily in what’s called a DNS cache to speed up future visits.
The DNS Time To Live (TTL) value determines how long that information is kept, which influences everything from website responsiveness to how quickly updates spread across the internet. Because of this, setting an appropriate TTL is important for ensuring a smooth and reliable browsing experience.
In the sections below, we explore DNS TTL in more detail and provide guidance on how to configure it effectively.
What is DNS TTL?
DNS TTL is a setting that defines how long cached DNS information (or DNS records) remain valid. In other words, it’s the “expiration timer” for cached DNS data. Once this data expires, the recursive DNS server (the part of the DNS system responsible for obtaining the IP address) has to fetch a fresh answer.
TTL is measured in seconds. A TTL of 300, for example, indicates that the response should be discarded after 300 seconds, or 5 minutes.
Why is TTL important in DNS and VPN usage?
TTL plays a key role in DNS performance and reliability. A properly configured TTL can speed up website loading, because cached DNS records allow the system to provide the IP address of a domain name without repeating the full translation process each time.
However, it’s also crucial to ensure that users see the most up-to-date version of a website or service; if cached DNS records aren't refreshed frequently enough, users may be directed to old IP addresses or outdated content.
This means that TTL settings are a balancing act: shorter TTLs ensure that updates to DNS records propagate quickly, which is critical for dynamic networks or services that change IP addresses frequently. Longer TTLs reduce the number of DNS queries, improving efficiency and reducing latency, but this comes at the cost of slower propagation of changes. Understanding this trade-off is key to maintaining both performance and accuracy in DNS resolution.
TTL also has implications for VPN users. Many VPNs rely on DNS records to direct devices to the correct VPN servers. If DNS TTLs are too long, these devices may continue trying to connect to outdated servers, resulting in delayed connections or failed logins. Proper TTL management ensures VPN clients quickly recognize changes to servers, maintaining fast and reliable connections.
High vs. low TTL: Pros and cons
Choosing the right TTL value involves balancing performance, update speed, and network load. High TTL values reduce the number of times the system needs to check IP addresses and can improve overall network performance. Users also experience faster connections for frequently visited websites because the system can often use stored addresses.
However, high TTLs also mean slower updates (longer DNS propagation time). If a website or VPN server changes IP addresses, users may continue trying to connect to the old address until the TTL expires. High TTLs can also prolong the effect of any malicious or corrupted cache entries caused by DNS cache poisoning or spoofing.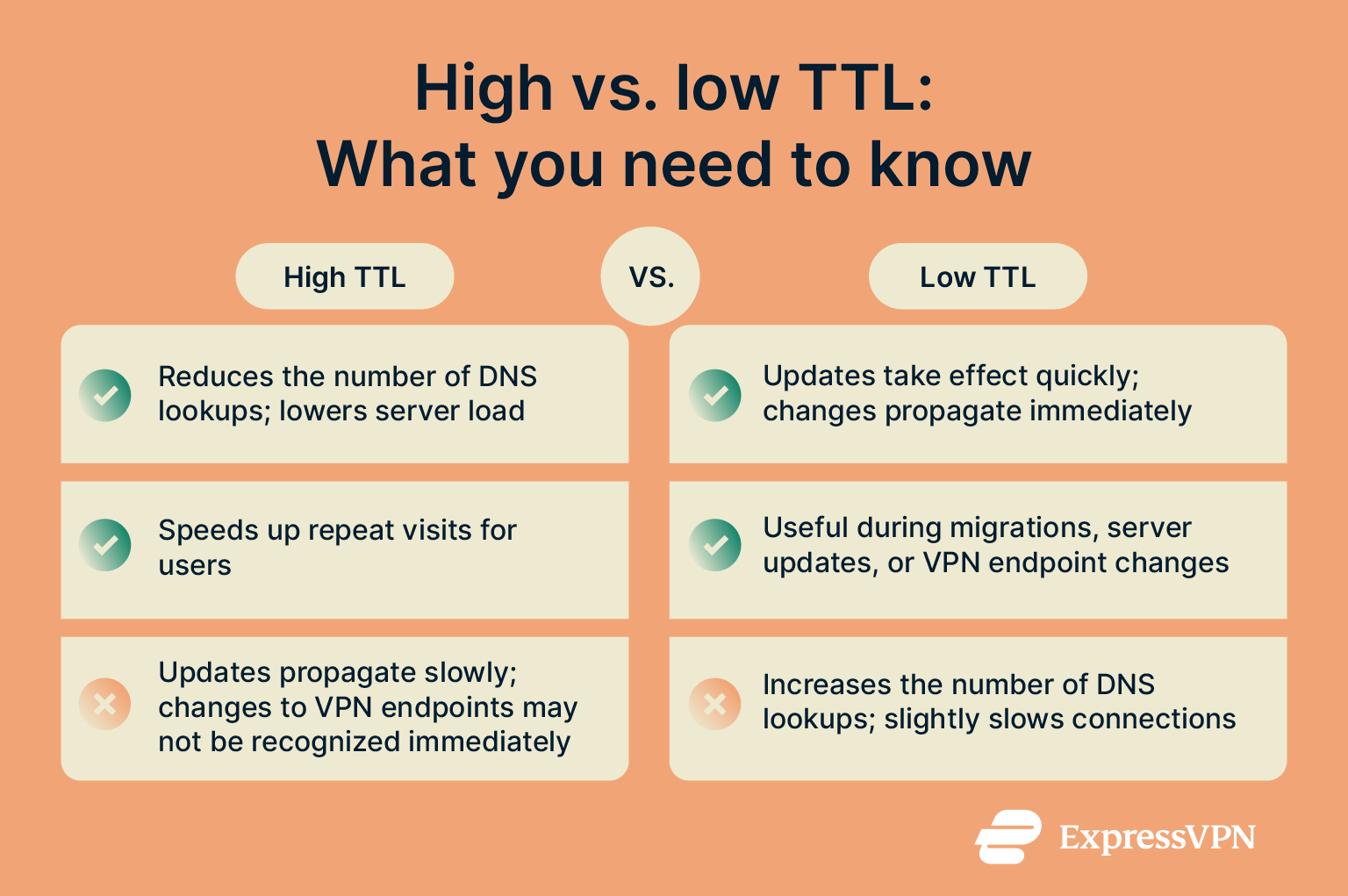
On the flip side, low TTL values allow changes to take effect quickly. This is especially useful during migrations or server updates to minimize disruptions. The trade-off is that low TTL values can increase server load and slightly slow connections, since the system is constantly updating its stored IP addresses.
Common TTL values and recommendations
If you manage a website or DNS records, understanding TTL values can help improve user experience, reduce server load, and control how quickly updates take effect.
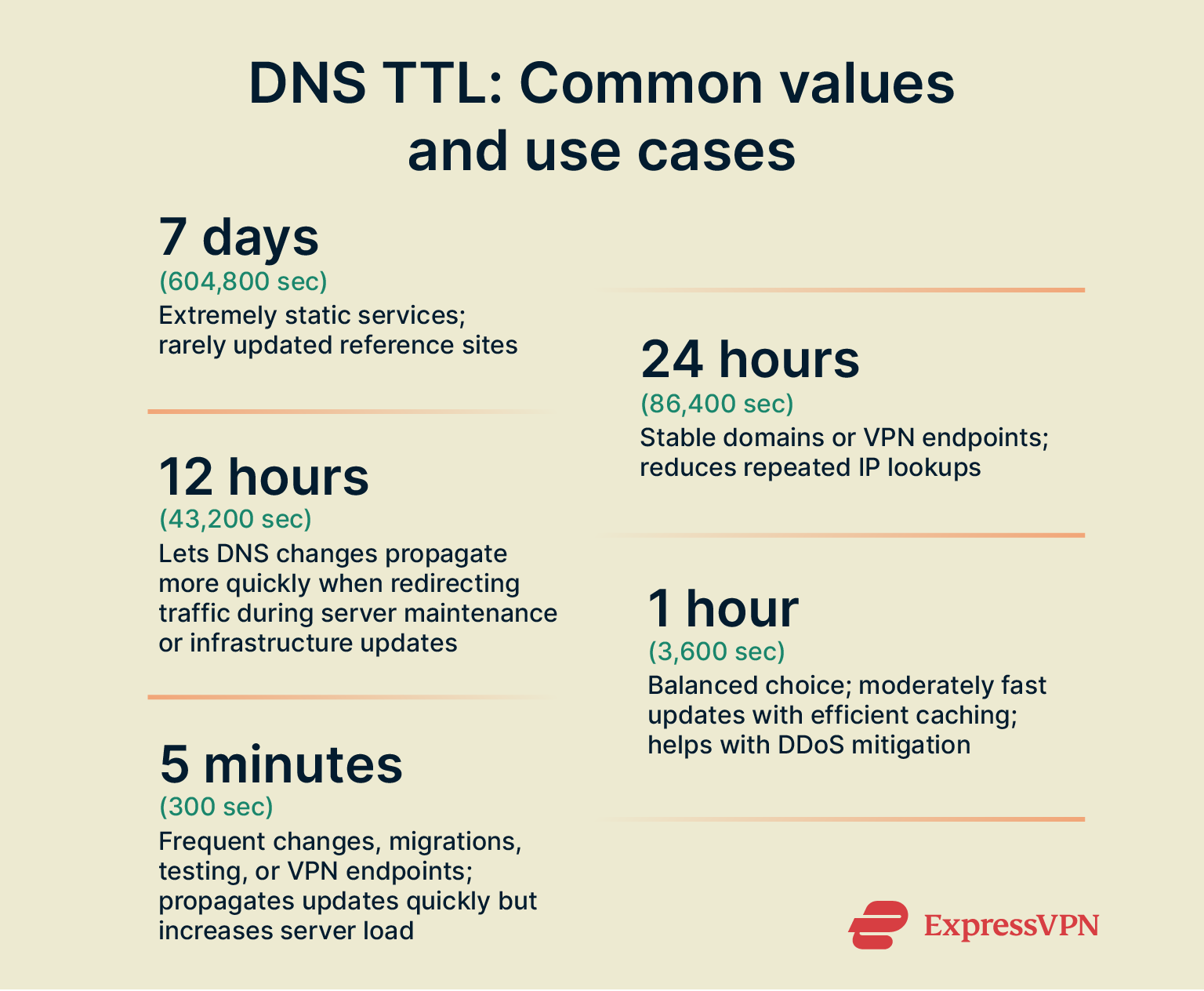
TTL values can vary widely depending on the use case. Default DNS TTL settings usually fall between 300 seconds (5 minutes) and 86,400 seconds (24 hours).
If you’re using a cloud service provider, check their guidelines, as they may have recommended TTL values tailored to their infrastructure. Otherwise, here are some values to consider:
- 7 days (604,800 seconds): TTL values rarely exceed 24 hours, but a weekly TTL may be used for extremely static services, such as reference sites.
- 24 hours (86,400 seconds): A daily TTL reduces repeated IP lookups and improves performance. It’s suitable for stable domains that rarely change.
- 12 hours (43,200 seconds): A TTL value that balances stability and flexibility. It allows DNS changes to propagate more quickly in situations like redirecting traffic during server maintenance or infrastructure updates, without overburdening server caches.
- 1 hour (3,600 seconds): A moderate TTL suitable for services that need faster updates but don’t require minute-to-minute responsiveness. It’s useful for planned or occasional changes, such as non-critical infrastructure updates, scheduled load balancing, or redirecting traffic in response to a distributed denial-of-service (DDoS) attack.
- 5 minutes (300 seconds): This value ensures changes propagate quickly, but it increases lookup frequency and server load. It’s ideal for migrations, testing, or urgent situations that require traffic to be redirected immediately, such as a server outage, network failure, or security incident.
Typical TTL settings for different DNS records (A, AAAA, CNAME, MX)
A DNS record tells computers how to find a website, email server, or other online service. Each record has a TTL, but the optimal TTL depends on the record type and how often it changes. Here’s an overview of the most common records and recommended TTL practices:
- A and AAAA records: These connect a domain name (like example.com) to a website’s IP address: A for IPv4 addresses, and AAAA for IPv6. If the website’s IP rarely changes, longer TTLs are used (hours or days). For services that may move or fail over frequently, meaning they automatically switch to a backup server if the primary server goes down, shorter TTLs (minutes) help users connect quickly to the correct IP.
- Canonical Name (CNAME) records: These are aliases that point one domain name to another. The alias itself usually stays the same, so typically, TTLs are moderate to long (hours or days).
- Mail Exchange (MX) records: These tell email systems where to deliver messages. Because mail servers rarely change, TTLs can be long (12–24 hours). That said, shorter TTLs can help when moving email servers quickly, so messages aren’t delayed.
- Name Server (NS) records: These specify which servers manage a domain’s DNS information. They rarely change, so TTLs are usually long, often measured in days.
DNS TTL best practices
DNS TTL settings play a key role in availability, scalability, and security. Whether you’re managing a website, a cloud application, or an internal network service (like a VPN), choosing the right TTL can improve user experience and operational flexibility. Below, we outline best practices for setting and managing TTLs in a variety of scenarios.
Use flexible TTLs for infrastructure changes
Set moderate TTLs (e.g., 1–4 hours) for services such as web apps, APIs, or VPN endpoints. These values allow updates to propagate quickly while keeping DNS query load manageable.
Additionally, before planned changes, such as moving a website to a new hosting provider, switching the IP of a VPN server, or repointing an API to a new backend service, temporarily lower TTLs (e.g., to 5–15 minutes) to ensure devices pick up new addresses promptly. After changes stabilize, raise the TTL again to reduce overhead.
Make TTL review part of your maintenance routine
TTL settings are often “set and forgotten,” but they should be reviewed whenever infrastructure changes occur. A mismatched TTL can cause old IPs to linger in caches, leading to failed logins, connection issues, or inconsistent behavior. If you've ever switched a server but some users still hit the old one hours later, it's likely because TTL wasn’t adjusted.
Plan TTLs for traffic surges and caching efficiency
For expected traffic spikes, such as product launches, software updates, or livestreams, longer TTLs can reduce the load on DNS servers by allowing devices to reuse cached DNS responses instead of sending repeated queries. Pairing this with a content delivery network (CDN) distributes content closer to users, ensuring performance and resilience even during heavy traffic.
Use TTLs to support security and privacy
In environments where DNS is part of a secure tunnel (e.g., VPNs or zero-trust networks), misconfigured DNS settings can leak queries. While TTLs don’t prevent leaks, they affect how fast fixes take effect once an issue is detected.
To reduce the risk of DNS leaks, use private or encrypted DNS resolvers inside the secure network and periodically verify DNS behavior with a DNS leak checker. If a leak is discovered, temporarily applying shorter TTLs can help configuration changes propagate more quickly.
Troubleshooting DNS TTL issues
Below we discuss some common issues related to DNS TTL and how to address them.
Length of time DNS takes to update
The time it takes for DNS changes to take effect depends on several factors, including the TTL values set for each record, internet service provider (ISP) caching policies, and general network conditions, which can differ based on the geographic location of users. This means that, even if you set very low TTLs, DNS changes may take some time to propagate, and not all users will see updates at the same time. Typically DNS propagation takes between 24 to 48 hours, but in some cases, it may take up to 72 hours.
This happens because DNS information is stored temporarily at multiple points across the internet. Each cache may hold an old copy of the record until its TTL expires, and some ISPs may refresh records less frequently than the TTL indicates. Registry updates, network routing, and general technical conditions can also add delays.
Although DNS propagation isn’t entirely within your control, you can take practical steps to speed things up:
- Lower the TTL before making changes: Reducing TTL values a few hours or a day in advance ensures cached entries expire sooner, helping updates spread more quickly. Once the update is complete, restore higher TTLs to reduce query load.
- Refresh public DNS caches: Large public DNS providers (e.g., Google Public DNS, OpenDNS) store cached records. Flushing or prompting an update from these services can help newer records reach users faster.
FAQ: Common questions about DNS TTL
What does TTL do in DNS setups?
Time to live (TTL) tells Domain Name System (DNS) resolvers how long to cache a record for before checking for updates. A short TTL means faster updates but more frequent lookups, while a long TTL reduces load but delays propagation.
How often should I review my DNS TTL settings?
Review time to live (TTL) whenever your infrastructure changes, and as part of regular maintenance. This ensures cached records don’t linger longer than intended. A quick review can prevent connection failures or slow propagation.
Does TTL affect email delivery?
Indirectly, yes. Email delivery depends on Domain Name System (DNS) records, such as Mail Exchange (MX) records. If those records are cached too long, mail servers may continue trying to deliver to an old address until the cache expires. Keeping time to live (TTL) set to appropriate values for how often your services change helps reduce the risk of delivery delays.
What’s the best TTL setting during server migration?
Use shorter time to live (TTL) before migration, so clients notice the new endpoint faster. After migration, you can increase TTL again to reduce unnecessary queries.
How to check DNS TTL on Windows, Mac, and Linux?
You can use the built-in command-line tool on your device. On Windows, use this command: nslookup -debug example.com; on Mac/Linux, use this command: dig exampledomain.com.
Can DNS TTL help prevent DNS leaks with VPNs?
Not directly. Time to live (TTL) only controls caching time, not where queries are sent. Preventing leaks requires ensuring the Domain Name System (DNS) stays inside the VPN tunnel and is encrypted. That said, shorter TTLs can help updates to DNS settings propagate faster if a misconfiguration occurs.
Can a short TTL improve VPN security against DNS spoofing?
It helps, but in a limited way. Short time to live (TTL) limits how long poisoned Domain Name System (DNS) data stays in caches, reducing risk if spoofing occurs. However, TTL alone doesn’t prevent spoofing; it just limits its duration. Real protection comes from using encrypted DNS inside the VPN tunnel and regularly testing for DNS leaks.
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN