BYOD security: What it is and why it matters

These days, more employees are using their own phones, tablets, and laptops for work. It’s quick, convenient, and often saves companies the cost of buying extra hardware. But letting personal devices into the workplace also brings new security challenges that can be tough to manage.
That’s why bring-your-own-device (BYOD) security is so important. It’s about making sure company data stays protected, even on devices the company doesn’t own. It involves clear policies, smart practices, and the right technology to keep your network safe without getting in anyone’s way.
In today’s hybrid work environments, solid BYOD security isn’t just a nice extra; it’s essential. This guide will walk you through what BYOD security is, why it matters, the main risks it addresses, and how organizations can manage those risks while still enjoying all the benefits of BYOD.
What is BYOD?
BYOD is a workplace approach that lets employees use their own personal devices (like phones, laptops, or tablets) for work tasks. Instead of relying on company-issued hardware, people can connect their own gear to company systems to check email, share files, use collaboration tools, or access cloud apps.
The idea is pretty straightforward: employees bring the devices they already own and use them to get work done. That could mean anything from checking Slack on your personal phone to editing a presentation on your home laptop. In many workplaces, BYOD has become the norm, especially with so many tools moving to the cloud and work happening from just about anywhere.
The rise of BYOD in the workplace
Over the last decade, BYOD has really taken hold in modern workplaces. Several trends have driven this growth:
- Remote and hybrid work: When offices closed during the 2020 pandemic, many people started working from home on their own devices. Even after returning to the office, a lot of them stuck with what was familiar and convenient.
- Employee preference: Many workers simply get more done on devices they know well. A Jamf survey found that 89% of employees would even take a pay cut to use their preferred hardware.
- Cost savings for businesses: BYOD cuts down on the need to buy, maintain, and replace company hardware, saving organizations money.
- Widespread cloud adoption: Most work tools (email, project management, file storage) now live in the cloud. As long as employees have secure credentials, they can access what they need from almost any device.
- Faster onboarding: New hires can hit the ground running with their own devices, without waiting for IT to set up new equipment.
Statistics show that 82% of organizations allow some form of BYOD. But as more people use their own devices for work, the risks grow, too. Personal devices don’t always meet the same security standards as company-issued hardware, which is why strong BYOD security is such a big focus for IT teams today.
And the trend isn’t slowing down. According to the BYOD Security Global Market Report 2025, the global market for BYOD security is expected to jump from $76.9 billion in 2024 to over $100 billion in 2025.
Why BYOD security matters
So what exactly makes BYOD security such a big deal? Here are the key challenges organizations have to keep in mind:
- Lack of security controls: Personal devices often don’t have the same protections as company-issued ones, like managed antivirus software or enforced updates. That can make them easier targets for malware, phishing, or unauthorized access.
- Data exposure: Sensitive files, emails, or client info can end up on a personal device that’s outside your company’s control. If that device is lost or hacked, so is the data.
- Compliance gaps: Regulations like the General Data Protection Regulation (GDPR) (Articles 5 and 32) and the Health Insurance Portability and Accountability Act (HIPAA) (45 CFR § 164.312) demand strong controls around how data is accessed, stored, and transmitted. If employees’ personal devices lack encryption, audit logging, or other security measures, you could end up out of compliance, especially if sensitive data is lost or exposed.
- Inconsistent configurations: Every employee’s device is different. Some might run outdated operating systems; others might have unvetted apps. IT teams can’t secure what they can’t see or standardize.
- Privacy and oversight issues: Employees naturally expect privacy on their own devices. But companies still need visibility into anything that touches company data. Without clear policies and boundaries, trust can break down, and so can security.
At the end of the day, every device that connects to your network is a potential entry point for threats. Without strong BYOD security in place, it only takes one weak link to compromise your systems, expose customer data, or trigger a regulatory violation.
Top BYOD security risks
So what exactly should IT teams watch out for? Here are the top security risks that come with BYOD.
1. Weak passwords
Weak or reused passwords are still one of the easiest ways for attackers to break in. If someone uses something simple like “Summer@2025” or reuses the same password everywhere, a breach in one place can quickly lead to another.
Attackers love this because they can run automated credential-stuffing attacks: trying known leaked passwords across corporate systems. It’s fast, quiet, and surprisingly effective.
According to LastPass, 81% of confirmed hacking-related breaches involve weak or stolen credentials. For businesses, that’s not just a statistic; it’s the single most preventable risk.
Learn more: Find out the best tips to create a strong password and keep your accounts secure.
2. Unsecured Wi-Fi networks
Public Wi-Fi networks often lack strong encryption and are open to eavesdropping or man-in-the-middle (MITM) attacks. Logging into a work account from a hotel or café without a virtual private network (VPN) could expose sensitive data to anyone snooping on the network.
Attackers sometimes even set up fake Wi-Fi hotspots with names like “Free_Cafe_WiFi” to trick people into connecting. Once you’re on their network, they can intercept logins, inject malicious content, or steal session cookies.
Even home Wi-Fi routers with default admin passwords or outdated firmware can be exploited remotely if not properly secured.
Tip: Set up a secure Wi-Fi guest network to share your internet access with anyone while protecting your personal data.
3. Outdated operating systems
That old phone or laptop might still work fine, but it’s an open invitation for attackers. No updates mean no security patches, so vulnerabilities stay wide open.
Once an unpatched device connects to your business apps or downloads sensitive documents, the risk spreads company-wide.
4. Malicious and unapproved apps (shadow IT)
Apps on personal devices don’t go through company security checks. Some are outright malicious, stealing data or tracking users in the background. Others might just be unapproved tools employees install on their own, creating blind spots for IT.
Sideloading (installing apps from outside official app stores) is especially risky because it skips app store security checks entirely. Even well-meaning but unapproved apps can store data insecurely, run outdated code, or share information with third parties. IT teams can’t monitor or patch what they don’t know exists.
5. Insufficient access controls
Without the right restrictions, personal devices can turn into easy backdoors. If everyone has the same level of access (regardless of their role, location, or device security), you lose control over who can see what.
A sales rep might get into financial records, or a part-time contractor might access internal tools. BYOD setups need clear rules to match access with trust.
6. Data leaks via cloud storage
Many personal devices automatically sync files to cloud accounts like Google Drive, iCloud, or Dropbox. A work document saved on a personal device might end up in a personal cloud account without anyone realizing it.
If those accounts aren’t secured or are shared with others, sensitive company data ends up in places IT can’t monitor or control. These aren’t flashy breaches, but they’re just as dangerous.
7. Lost or stolen devices
If someone loses their device and there’s no lock screen, no encryption, and no remote wipe, it’s basically an instant breach. Work emails, shared drives, credentials: everything could be accessible within minutes.
Lost devices in airports, cafés, or cabs are more common than most teams realize. And if there’s no clear process for containing the damage, the fallout can last.
8. Social engineering attacks
Personal devices blur the line between work and personal use, making employees more vulnerable to phishing and other social engineering scams. A fake email, SMS, or browser pop-up can easily trick someone into handing over their credentials or other sensitive information.
BYOD setups often don’t have the same security filters that corporate machines do, giving attackers an easier way in.
Learn more: Want to help your team spot these scams? Check out the most common phishing email red flags to stay ahead of the tricks attackers use.
9. Incomplete offboarding
When someone leaves the company but still has work access on their phone or laptop, that’s a big risk. Without clear offboarding steps (like revoking tokens, removing access, or wiping work apps), they may keep sensitive emails, files, or tools they shouldn’t have anymore.
In BYOD setups, this step is often missed or delayed, leaving the door open long after someone’s gone.
BYOD security measures and technologies
How do you reduce the risks of employees using their own devices for work without invading their privacy? The goal isn’t to control the entire device but to secure the parts that touch company data. Here are some of the key technologies and practices that make BYOD safe and manageable.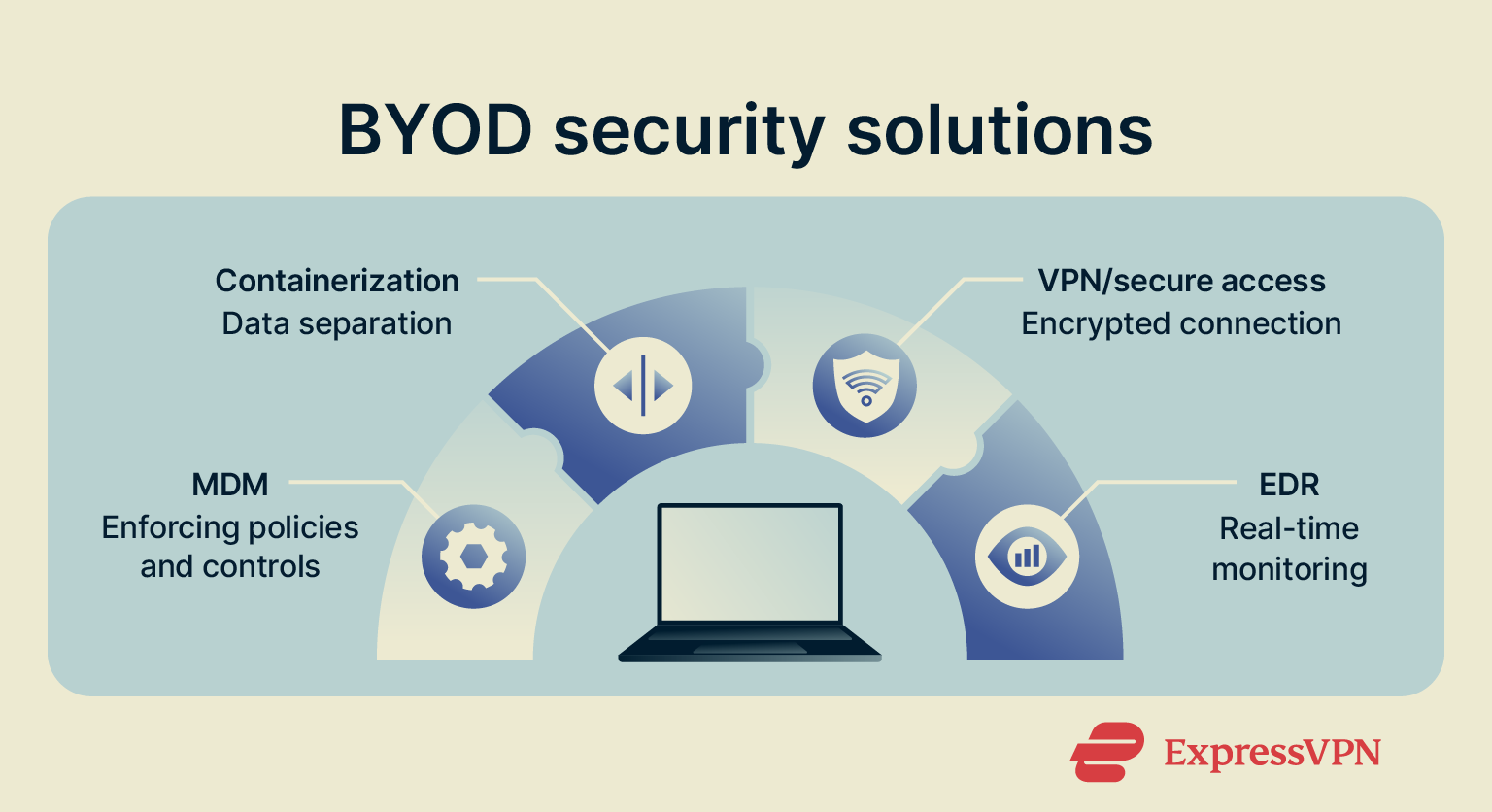
Mobile device management (MDM)
MDM platforms help IT teams apply security policies to employee-owned devices without interfering with personal files. When a device is enrolled, it gets a management profile that enforces specific protections in the background.
- Policy enforcement: IT can push settings like minimum password length or auto-lock timers. If a device doesn’t meet the rules, it can be blocked from accessing company email or VPN until it’s fixed.
- App management: MDM can allow or block specific apps, install and update approved apps remotely, or offer an enterprise app store for employees.
- Remote wipe: If a device is lost or an employee leaves the company, business data can be wiped remotely, while personal photos, messages, and other files stay untouched.
- Work/personal separation: MDM can set up separate work profiles or secure containers, keeping company data isolated from personal apps.
- Visibility and inventory: IT teams get an overview of OS versions, security patch levels, and overall device health to ensure everything stays compliant.
For a successful rollout, it’s essential to communicate clearly with employees, letting them know exactly what’s monitored, what’s not, and how their personal privacy is protected.
Containerization and data separation
While MDM handles overall device management, containerization is all about creating a secure, separate space on personal devices just for work stuff. Think of it as a special work-only zone on your phone or tablet where company data and apps live.
The big benefit? Data can’t easily move between the work side and the personal side. So you can’t accidentally drop a confidential file into your personal downloads, and IT can’t peek at your private photos or messages. It’s designed to prevent accidental leaks while respecting employee privacy.
Common ways companies do this include:
- Work profiles: Android Enterprise supports a parallel user space with managed apps and restricted data flow.
- Encrypted containers: Solutions like Samsung Knox create a secure zone that needs user authentication before you can get in.
- Secure workspace apps: These act like virtual desktops, keeping work apps and data isolated from the rest of the device.
- Sandboxed enterprise apps: These are secure email or file apps designed to work only with other approved work apps, preventing copy/paste or file transfers to personal apps and keeping company data safely separated.
With containerization in place, someone’s family can borrow the device without ever accessing company files, and a misdirected upload won’t dump corporate data into a personal cloud account. It’s a key way to prevent unintentional leaks while giving employees peace of mind about their privacy.
Virtual private networks (VPNs) and secure network access
When employees use their own devices to connect to work resources, the network they’re on really matters. Public Wi-Fi in hotels, airports, or cafés is rarely secure, and even home routers aren’t always fully safe. A VPN helps by encrypting traffic, making it harder for attackers to spy on sensitive data.
Common approaches include:
- Enterprise VPN for internal systems: Companies often require BYOD users to connect through a corporate VPN before accessing internal tools like intranets, file servers, or admin dashboards. This ensures company data travels through an encrypted tunnel and lets IT enforce access policies, monitor usage, and block suspicious activity.
- Personal VPN for remote work: Even if employees aren’t using internal company systems, a personal VPN like ExpressVPN can help secure their internet traffic when working from untrusted locations. It encrypts everything leaving the device, protecting connections to cloud apps like Google Drive, Slack, or email, even when using public Wi-Fi.
- Split tunneling: It lets employees route only work-related traffic through the VPN while everything else uses the normal internet connection. This helps with speed and bandwidth, since personal browsing doesn't slow down the secure connection.
- Zero-trust network access (ZTNA): ZTNA tools offer an alternative to traditional business VPNs. Instead of giving a device full network access, they grant permission to specific apps only after verifying user identity, device health, and location. It’s more precise, improves security, and limits exposure if something goes wrong.
- Secure gateways: Often used alongside VPN or ZTNA, these tools check devices for updates, antivirus, or encryption before allowing access, ensuring only secure, compliant devices can connect
Endpoint detection and response (EDR)
EDR tools provide real-time threat detection, continuous monitoring, and automated responses to help protect employee devices, even when they’re outside the office network. They’re designed to spot suspicious behavior quickly and contain threats before they spread. In BYOD environments, EDR typically offers:
- Behavioral analysis: Detects abnormal patterns like ransomware activity, unauthorized data access, or unusual process behavior.
- Automated incident response: Can isolate affected devices, stop malicious processes, or quarantine harmful files without needing user action.
- Remote forensics: Tracks what happened on a device (including which apps ran or what files were accessed) to support remote investigations, even if the device isn’t on the corporate network.
EDR tools that offer cloud-based management and strong behavioral detection are especially useful for BYOD setups, since employees often work from different locations. At minimum, companies should provide or require a next-generation antivirus solution with these capabilities.
When combined with other measures, EDR becomes an essential part of a layered security approach that keeps company data safe without compromising employee privacy or flexibility.
BYOD security best practices for organizations
Technology alone isn’t enough to keep BYOD setups secure. Companies also need clear policies and ongoing practices to make sure everything stays secure, compliant, and easy to understand. Here are the essentials:
Create a clear BYOD policy
A strong BYOD policy lays out the ground rules right from the start. It should be clear about what’s allowed, what’s required, and what happens if there’s a problem. A good BYOD policy should be written in plain, easy-to-understand language. Include it as part of onboarding, and review it during security training or after any incidents. Here are some key elements to include:
A good BYOD policy should be written in plain, easy-to-understand language. Include it as part of onboarding, and review it during security training or after any incidents. Here are some key elements to include:
- Eligible devices: Specify which personal devices and operating systems are permitted.
- Security requirements: Set expectations for basics like passcodes, encryption, antivirus software, regular updates, and possibly enrolling in MDM.
- Acceptable use: Make sure employees know work files shouldn’t be stored in personal cloud accounts or shared through unapproved apps.
- Privacy boundaries: Explain clearly what IT can and can’t see (typically just work profiles or containers, not personal photos or messages).
- Data ownership: Clarify that all company data remains company property and may be removed remotely if needed.
- Support and liability: Let employees know what IT will support and be clear that damage to personal devices is their responsibility.
- Monitoring and compliance: Mention any device checks or logging that’s needed to meet legal or regulatory requirements.
- Policy violations: Explain what happens if someone breaks the rules, and require employees to acknowledge and agree to the policy.
Educate employees on security hygiene
You can’t protect what people don’t understand. Teaching employees about security helps them take ownership of their role in keeping company data safe.
Start with regular training on topics like phishing, strong passwords, Wi-Fi safety, and app security. Keep it practical and relatable: use real-world examples and short refreshers throughout the year. Simulated phishing tests are also really effective, as long as you follow up with quick, helpful feedback if someone clicks on a fake email.
Make security easy to remember. Give employees a simple cheat sheet with key dos and don’ts, like always using a VPN on public Wi-Fi and reporting lost devices right away. You can also send out quick security alerts or reminders when there’s a new mobile threat going around.
Most importantly, reinforce that proper security protects both company data and employees’ personal information. And if something seems off (like a strange app or a suspicious link), make sure they know how to report it without worrying about getting in trouble.
Restrict access based on role and compliance
Not everyone in the company needs access to everything, and not every personal device should be trusted the same way. Good BYOD security means thinking carefully about who can see what and under what conditions. Here are some practical ways to do that:
- Role-based control: Only give people access to what they need for their job. A salesperson might need access to the Customer Relationship Management (CRM) but not HR records.
- Sensitive system restrictions: Block personal devices from reaching critical systems like finance tools or source code repositories.
- Conditional access: Make sure devices meet minimum standards, like having encryption, screen locks, and antivirus, before they can connect.
- Network isolation: Keep BYOD devices on separate networks or virtual local area network (VLAN) so they have limited access to other company systems.
- Contextual rules: Add smart restrictions based on things like time of day or location. For example, flagging or blocking logins from overseas IP addresses.
- Granular app access: Allow access to specific services employees need without exposing the entire company network.
Prepare for lost or compromised devices
Things happen. Devices get lost or hacked, but with a good plan in place, those situations don’t have to turn into disasters.
Start by making sure employees know exactly what to do if something goes wrong. If a device is lost, they should know to contact IT right away. From there, IT can trigger remote wipe or lock functions and suspend access to work apps or email.
If a device is compromised (like infected with malware), the plan should include steps to isolate it, run scans, and escalate the issue to the security team. And if that device had access to sensitive data, you might need to involve legal or compliance teams.
Keep people productive by offering fallback options like virtual desktops or loaner devices so they can keep working while their personal device is handled. Make sure to log every incident so you can spot patterns and improve policies over time.
Finally, don’t just close the case and move on. Follow up with the employee. Clarify any policy gaps, provide retraining if needed, and make sure everyone feels confident about what to do next time. A well-rehearsed response plan reduces panic, limits the damage, and helps everyone trust the system.
FAQ: Common questions about BYOD security
What is BYOD in cybersecurity?
Bring your own device (BYOD) refers to employees using their personal phones, laptops, or tablets to access company systems or data. BYOD security is the set of policies and tools that protect business information on those devices.
Since the devices aren’t company-owned, the challenge is to apply controls without overreaching into personal content.
What does a good BYOD policy include?
A strong policy outlines what devices are allowed, what protections they need, and what happens if something goes wrong. It should cover encryption, passcodes, acceptable use, data ownership, privacy limits, and offboarding. Clear rules up front make bring your own device (BYOD) safer and easier to manage.
Is BYOD safe for small businesses?
It can be, if done right. Small teams can still require basics like device encryption, virtual private network (VPN) use, and secure passwords. Most bring-your-own-device (BYOD) risks come from a lack of structure, not a lack of size. A few simple steps go a long way.
What tools help enforce BYOD security?
Mobile device management (MDM), virtual private networks (VPNs), and secure containers are key. MDM enforces policies remotely. VPNs protect traffic on public networks. Containers separate work data from personal apps. Together, these tools give you control without invading privacy.
How to make BYOD secure?
Start with education and a clear policy. Then add controls: limit access by role, require compliant devices, isolate bring your own device (BYOD) on separate networks, and use tools like mobile device management (MDM) or zero-trust network access (ZTNA). If something feels off, employees should know how to report it fast.
What are the risks of BYOD?
Lost devices, weak passwords, outdated software, and rogue apps are all common. Files might sync to personal clouds, or access might linger after someone leaves. Because bring your own device (BYOD) sits outside IT’s full control, even small mistakes can open big gaps.
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN