-
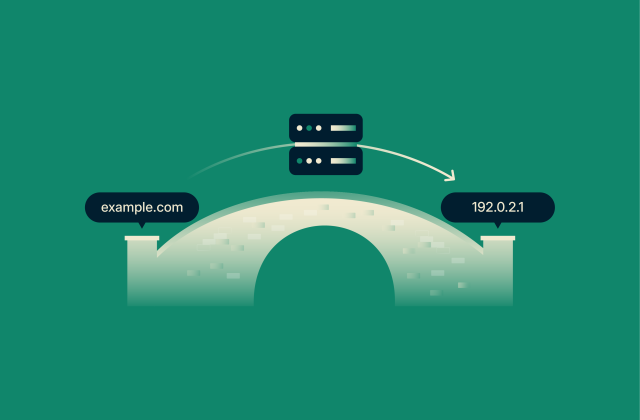
Nameserver: The complete guide to setup, management, and troubleshooting
Nameservers are essential for any functioning website or email domain. Without proper nameserver configuration, emails wouldn't reach their destinations, and visitors would encounter loading errors wh...
-

Zeus virus (Zbot malware): What it is and how to stay protected
The Zeus virus is best known for fueling large-scale financial cybercrime and stealing banking credentials. Although the original Zeus virus is no longer active, it spawned numerous variants that rema...
-
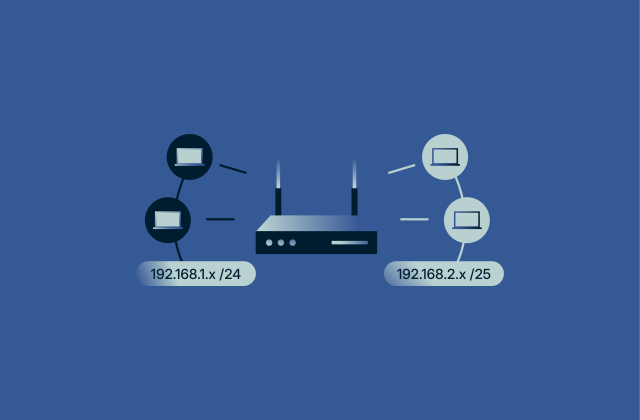
What is a subnet mask? Why it matters for your network
Every device on a network needs a way to know where information should go. Without clear rules, data would move blindly, causing confusion and slowdowns. Subnet masks are one of the tools that make ne...
-

Connected but no internet access: Why it happens and how to fix it
Getting a message stating that you’re connected but have no internet access can be frustrating. If your network is fine, why won’t websites load? It’s often unclear what has caused this error me...
-

How to block a TikTok account: A step-by-step guide
TikTok can be fun, but it also has people you might not want around. Maybe someone keeps dropping comments you don’t like, maybe they flood your DMs, or maybe their videos just won’t stop showing ...
-

How to delete your WhatsApp account (step-by-step guide)
Whether you’re done with WhatsApp for good or just taking a break, the process of deleting your account is relatively quick and easy. This guide will show you exactly how to delete or uninstall your...
-

Data harvesting: What it is and how to stay protected
Data harvesting is the process of collecting large amounts of personal or organizational information online. Companies, websites, and apps gather this data to analyze behaviors, target advertising, or...
-

What is network mapping? Complete guide to tools and security best practices
Network mapping is the creation of a visual map of devices and connections in a network. It’s an essential step in managing any modern network, as it’s what makes it possible to actually understan...
-

PPTP vs. L2TP: What’s the difference?
Point-to-Point Tunneling Protocol (PPTP) and Layer 2 Tunneling Protocol (L2TP) are both virtual private network (VPN) tunneling protocols, but they function very differently. All VPNs direct internet ...
-

Log4Shell vulnerability: What it is and how to stay protected
The Log4Shell vulnerability gained global attention when it was discovered in late 2021. Affecting the widely used Log4j logging library, this flaw made it dangerously easy for attackers to remotely e...
Featured




